Step 1:
After downloading the zip file and extracting it. we will find an image jpg file.
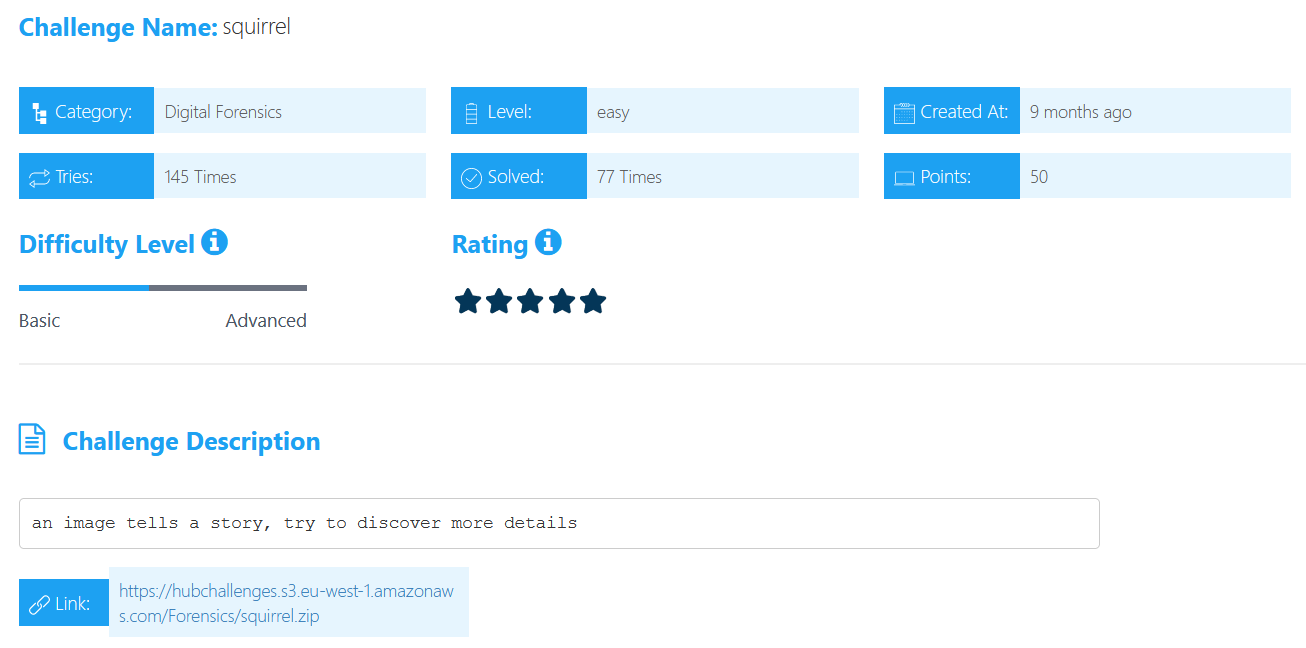
By passing the image file to strings command strings squirrel.jpg | less, we will observe a link to download another file.
Step 2:
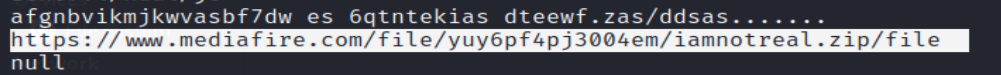
After downloading the zip file, we will find that it is protected by a password.
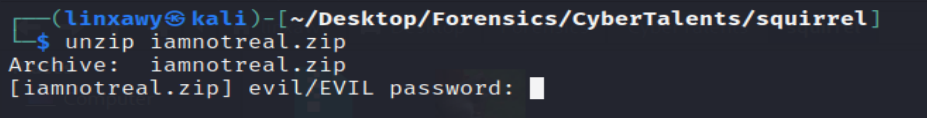
So let’s use zip2john tool and see if we are able to crack the password or not.
Getting hash of zip file :
Running rockyou.txt wordlist to crack the password hash
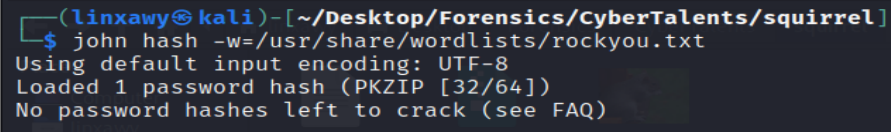
Since I have cracked this hash before so let’s use the --show option to display the password.
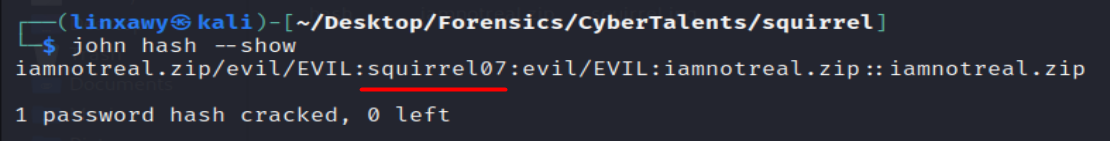
Zip file password : squirrel07
Step 3:
Passing EVIL file to file command, we will observe that it can’t recognize the type of it’s data.
So I decided to check the hexdump of this file in order to check the magic bytes of it.
using this command : xxd -g 1 EVIL | less
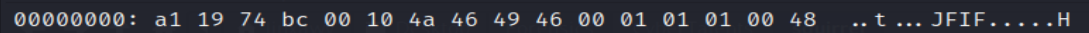
We will find that the first 4 bytes are corrupted according to the JFIF file signature.
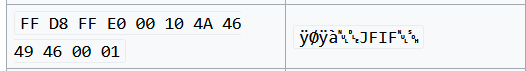
Modifying these bytes by any hexeditor tool, I have used ghex then changed the file extension to EVIL.jfif.
Step 4:
Opening the image file after we have modified the corrupted bytes and changed its extension, we will see a text in top-right corner.

Copying this text and using CyberChef, It will detect that it is a base32 encoding text.
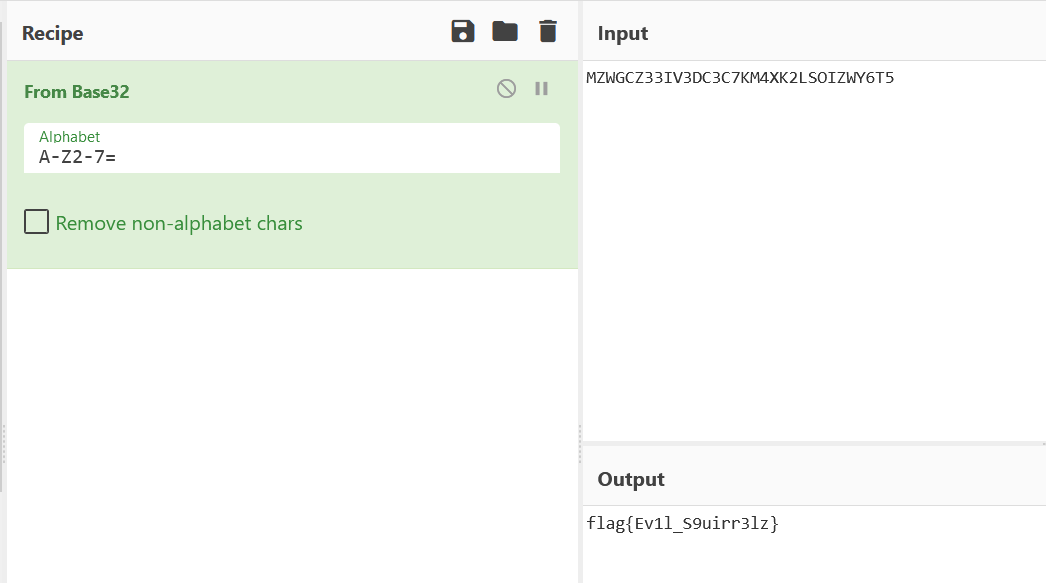
Decoding the text from base32 and we will find the flag : flag{Ev1l_S9uirr3lz}